How to Allow Remote Management of Cisco ASA 5510 Firewall
How do I actually configure the firewall to allow remote administration via Telnet, SSH, or HTTPS/ASDM?
Solution
Cisco ASA Allow Telnet - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine, or a whole network, the syntax is "telnet {ip address} {subnet mask} {interface that its connected to}.
The following will just allow one host (192.168.1.10).
PetesASA(config)#
PetesASA(config)#telnet 192.168.1.10 255.255.255.255 inside
PetesASA(config)#
The following will just allow a whole network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#telnet 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. To set the password you use the "passwd" command (yes that's spelled correctly).
PetesASA(config)#
PetesASA(config)#passwd PASSWORD123
PetesASA(config)#
4. By default the telnet session times out after 5 mins, I prefer to change this to 45 minutes.
PetesASA(config)#
PetesASA(config)#telnet timeout45
PetesASA(config)#
5. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Allow Telnet - Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK. (Note you can set the timeout on this page also).
Cisco ASA Allow SSH - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine, or a whole network, the syntax is "ssh {ip address} {subnet mask} {interface that its connected to}.
The following will just allow one external host (123.123.123.123).
PetesASA(config)#
PetesASA(config)#ssh 192.168.1.10 255.255.255.255 outside
PetesASA(config)#
The following will just allow a whole internal network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#ssh 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. To set the password you use the "passwd" command (yes that's spelled correctly).
PetesASA(config)#
PetesASA(config)#passwd PASSWORD123
PetesASA(config)#
4. By default the SSH session times out after 5 mins, I prefer to change this to 45 minutes.
PetesASA(config)#
PetesASA(config)#ssh timeout45
PetesASA(config)#
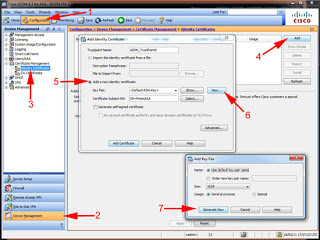
5. To encrypt the SSH access you need to have a certificate on the firewall, (Note: this certificate is made from the firewall's host name and its domain, if you ever change either, the certificate will break, and SSH access will cease until the certificate is re-created). To create a key issue a "crypto key generate rsa" command.
PetesASA(config)# crypto key generate rsa
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
PetesASA(config)#
6. UPDATE Be aware, all ASA devices running an operating system of 8.4(2) or newer, you can NO LONGER LOG IN WITH A USERNAME OF PIX, and the telnet password, youHAVE TO define a username and password, then enable AAA Authentication for SSH.
PetesASA(config)# aaa authentication ssh console LOCAL
PetesASA(config)# username admin password Password123 privilege 15
7. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA Allow SSH - Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select SSH > Supply the IP and subnet > OK. (Note you can set both the timeout, and the SSH versions you will accept, on this page also). Note you still need to generate the RSA Key (See step 5 above, good luck finding that in the ASDM - drop to command line and do it).
UPDATE Be aware, all ASA devices running an operating system of 8.4(2) or newer, you can NO LONGER LOG IN WITH A USERNAME OF PIX, and the telnet password, youHAVE TO define a username and password, then enable AAA Authentication for SSH.
Cisco ASA - Enable AAA for SSH (Local Database) ASDM version 6.4(7)
Cisco ASA - Add a User to the Local Database
Cisco ASA - Allow HTTPS/ASDM - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine or a whole network, the syntax is "http {ip address} {subnet mask} {interface that it's connected to}.
The following will just allow one host (192.168.1.10).
PetesASA(config)#
PetesASA(config)#http 192.168.1.10 255.255.255.255 inside
PetesASA(config)#
The following will just allow a whole network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#http 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. Unlike telnet and ssh, HTTPS/ADSM access is via the firewalls enable password (Unless you have enabled AAA logon). this password is set with the "enable password {password}" command. (Note: You will already have entered this password in step 1, only do this if you wish to change it).
PetesASA(config)#
PetesASA(config)#enable password PASSWORD123
PetesASA(config)#
4. You need to make sure that HTTPS access is enabled with a "http server enable" command.
PetesASA(config)#
PetesASA(config)#http server enable
PetesASA(config)#
Note: if your port forwarding https on your firewall you will NOT be able to get access externally unless you put it on a different port (i.e.1234).
PetesASA(config)#
PetesASA(config)#http server enable 1234
PetesASA(config)#
5. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA - Allow HTTPS/ASDM - Via ASDM (version shown 6.4(7))
OK, the title of this might raise an eyebrow, but if you have access to the ASDM and you want to grant access to another IP/Network them you might want to do this. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select ASDM/HTTPS > Supply the IP and subnet > OK. (Note: You can also enable and disable the http Server here and change its port number).
Cisco ASA - Allow Remote Management over a VPN
Whether you are on a client VPN session or assessing the firewall via a site to Site VPN. To manage the firewall (via Telnet/SSH/ASDM) you need to 'enable the management interface'
Cisco ASA - Allow Remote Management over a VPN - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Enable remote management with the following command;
PetesASA(config)#management-access inside
3. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA - Allow Remote Management over a VPN via ASDM (version shown 6.4(7))
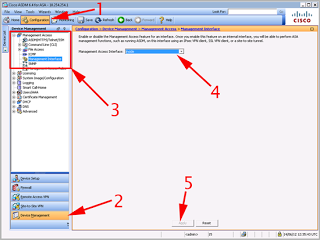
Connect via ASDM > Navigate to Configuration > Device Management > Management Access > Management Interface > Set Management Access Interface to "Inside" > Apply > File > Save running Configuration to flash.
END------------------------
Thanks for Watching my Blog :-)
How do I actually configure the firewall to allow remote administration via Telnet, SSH, or HTTPS/ASDM?
Solution
Cisco ASA Allow Telnet - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine, or a whole network, the syntax is "telnet {ip address} {subnet mask} {interface that its connected to}.
The following will just allow one host (192.168.1.10).
PetesASA(config)#
PetesASA(config)#telnet 192.168.1.10 255.255.255.255 inside
PetesASA(config)#
The following will just allow a whole network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#telnet 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. To set the password you use the "passwd" command (yes that's spelled correctly).
PetesASA(config)#
PetesASA(config)#passwd PASSWORD123
PetesASA(config)#
4. By default the telnet session times out after 5 mins, I prefer to change this to 45 minutes.
PetesASA(config)#
PetesASA(config)#telnet timeout45
PetesASA(config)#
5. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Allow Telnet - Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK. (Note you can set the timeout on this page also).
Cisco ASA Allow SSH - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine, or a whole network, the syntax is "ssh {ip address} {subnet mask} {interface that its connected to}.
The following will just allow one external host (123.123.123.123).
PetesASA(config)#
PetesASA(config)#ssh 192.168.1.10 255.255.255.255 outside
PetesASA(config)#
The following will just allow a whole internal network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#ssh 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. To set the password you use the "passwd" command (yes that's spelled correctly).
PetesASA(config)#
PetesASA(config)#passwd PASSWORD123
PetesASA(config)#
4. By default the SSH session times out after 5 mins, I prefer to change this to 45 minutes.
PetesASA(config)#
PetesASA(config)#ssh timeout45
PetesASA(config)#
5. To encrypt the SSH access you need to have a certificate on the firewall, (Note: this certificate is made from the firewall's host name and its domain, if you ever change either, the certificate will break, and SSH access will cease until the certificate is re-created). To create a key issue a "crypto key generate rsa" command.
PetesASA(config)# crypto key generate rsa
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
PetesASA(config)#
6. UPDATE Be aware, all ASA devices running an operating system of 8.4(2) or newer, you can NO LONGER LOG IN WITH A USERNAME OF PIX, and the telnet password, youHAVE TO define a username and password, then enable AAA Authentication for SSH.
PetesASA(config)# aaa authentication ssh console LOCAL
PetesASA(config)# username admin password Password123 privilege 15
7. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA Allow SSH - Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select SSH > Supply the IP and subnet > OK. (Note you can set both the timeout, and the SSH versions you will accept, on this page also). Note you still need to generate the RSA Key (See step 5 above, good luck finding that in the ASDM - drop to command line and do it).
UPDATE Be aware, all ASA devices running an operating system of 8.4(2) or newer, you can NO LONGER LOG IN WITH A USERNAME OF PIX, and the telnet password, youHAVE TO define a username and password, then enable AAA Authentication for SSH.
Cisco ASA - Enable AAA for SSH (Local Database) ASDM version 6.4(7)
Cisco ASA - Add a User to the Local Database
Cisco ASA - Allow HTTPS/ASDM - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Now you can either allow access for one machine or a whole network, the syntax is "http {ip address} {subnet mask} {interface that it's connected to}.
The following will just allow one host (192.168.1.10).
PetesASA(config)#
PetesASA(config)#http 192.168.1.10 255.255.255.255 inside
PetesASA(config)#
The following will just allow a whole network 192.168.1.1 to 254
PetesASA(config)#
PetesASA(config)#http 192.168.1.0 255.255.255.0 inside
PetesASA(config)#
3. Unlike telnet and ssh, HTTPS/ADSM access is via the firewalls enable password (Unless you have enabled AAA logon). this password is set with the "enable password {password}" command. (Note: You will already have entered this password in step 1, only do this if you wish to change it).
PetesASA(config)#
PetesASA(config)#enable password PASSWORD123
PetesASA(config)#
4. You need to make sure that HTTPS access is enabled with a "http server enable" command.
PetesASA(config)#
PetesASA(config)#http server enable
PetesASA(config)#
Note: if your port forwarding https on your firewall you will NOT be able to get access externally unless you put it on a different port (i.e.1234).
PetesASA(config)#
PetesASA(config)#http server enable 1234
PetesASA(config)#
5. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA - Allow HTTPS/ASDM - Via ASDM (version shown 6.4(7))
OK, the title of this might raise an eyebrow, but if you have access to the ASDM and you want to grant access to another IP/Network them you might want to do this. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select ASDM/HTTPS > Supply the IP and subnet > OK. (Note: You can also enable and disable the http Server here and change its port number).
Cisco ASA - Allow Remote Management over a VPN
Whether you are on a client VPN session or assessing the firewall via a site to Site VPN. To manage the firewall (via Telnet/SSH/ASDM) you need to 'enable the management interface'
Cisco ASA - Allow Remote Management over a VPN - Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
User Access Verification
Password:
Type help or '?' for a list of available commands.
PetesASA> en
Password: ********
PetesASA# configure terminal
PetesASA(config)#
2. Enable remote management with the following command;
PetesASA(config)#management-access inside
3. Lastly, save the changes with a "write mem" command.
PetesASA# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
PetesASA#
Cisco ASA - Allow Remote Management over a VPN via ASDM (version shown 6.4(7))
Connect via ASDM > Navigate to Configuration > Device Management > Management Access > Management Interface > Set Management Access Interface to "Inside" > Apply > File > Save running Configuration to flash.
END------------------------
Thanks for Watching my Blog :-)





Comments
Post a Comment